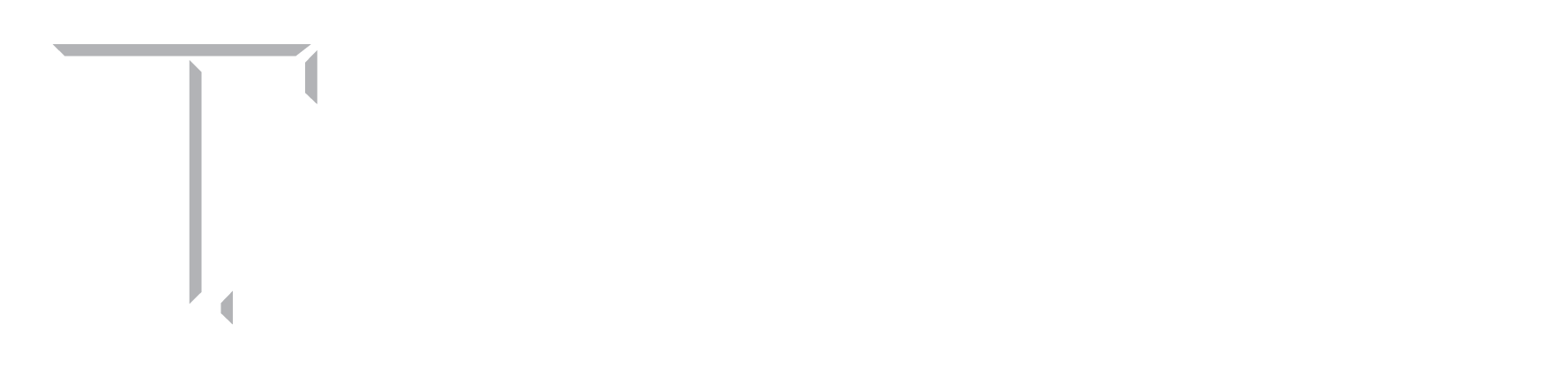① Hardware Fuzzing
Hardware Fuzzing for Processor Designs
The increasing complexity of modern processors poses many challenges to existing hardware verification tools and methodologies for detecting security-critical vulnerabilities. Recent attacks on processors have shown the fatal consequences of uncovering and exploiting hardware vulnerabilities, such as Meltdown and Spectre. Fuzzing has emerged as a promising technique for detecting vulnerabilities. We design and implement hardware fuzzers that (i) are compatible with industrial IC design verification flow; (ii) are scalable to real, complicated, industrial-designs with several tens of thousands of code; (iii) capture many intrinsic hardware behaviors using multiple coverage metrics: toggle, branch, FSM, etc.; (iv) do not require design specifications; and (v) detects several vulnerabilities that lead to severe security exploits. Our first hardware fuzzer, TheHuzz achieved 1.98× the speed compared to the industry-standard random regression approach and detected 11 bugs in four popular open-source RISC-V and OpenRISC processors, including eight new bugs.
Hack@EVENT
Hack@EVENT is the world’s largest joint industry-academia hardware security competition. It aims to motivate security community in developing techniques that identify vulnerabilities more efficiently in SoCs. Participating teams will receive real-world RISC-V SoCs with security features and vulnerabilities inserted. Teams need to ensure the security specification of the given SoC by identifying security vulnerabilities, assessing their impact, providing exploits, and proposing mitigation. They are free to use any tools or techniques and should provide a detailed report on their findings. For more information about the competition and eligibility requirements, visit https://hackatevent.org/
Organizers:




② AI for Hardware Security
Research
A constant attack-defense cycle has been going on for the past two decades of research in hardware security. The conceptualization of attack/defense techniques usually involves ad-hoc analyses of specific defense/attack formulations. Given an attack/defense technique implemented for a design, researchers ascertain the efficacy of the underlying attacks/defenses against known (and available) defenses/attacks. In the process, researchers follow a cat-and-mouse game where one group proposes an attack, and another group develops a defense to thwart the attack. Another group defends, only to be thwarted again, and so on. Each interaction of this back-and-forth usually takes about a year. Hence, arriving at a robust and acceptable solution takes several years and sometimes even more than a decade.
To alleviate this problem, our objective is to reduce the time to arrive at a robust and acceptable solution from years to months or possibly weeks. To that end, our research leverages supervised, unsupervised, and reinforcement learning techniques to develop and evaluate novel attacks/defenses in an automated, scalable, effective, and efficient fashion. By doing so, we have designed novel attacks/defenses that outperform all prior works devised over more than a decade. For instance, we developed an RL-based technique that outperforms all prior work on detecting hardware Trojans by a factor of 169✖️. In another direction, we also created a novel attack RL agent that thwarts all defenses developed over a decade of research in hardware Trojans. We are also exploring the potential of RL to solve other hardware security problems, such as fault injection. Our team has developed an RL agent that automatically explores the vast search space of block ciphers to find exploitable fault models. Our agent finds all fault models manually discovered by human experts over the years. What’s more surprising is that, for a popular block cipher, it also finds a novel fault model not found by any human expert!
Currently, we are working on developing similar techniques for other hardware security problems too.
Outreach – AI vs. Humans Competition
To train current and future generations of security researchers, we launched the AI vs. Humans competition in 2022 as a part of CSAW. The competition is developed to train researchers to defeat AI-based tools developed for hardware security. In this competition, participants can play the role of a defender, attacker, or both! The objective for the attacker is to inject stealthy hardware Trojans that evade state-of-the-art AI-based detection tools. For the defender, the objective is to generate test patterns that detect our AI-generated hardware Trojans. The participants are encouraged to use tools and techniques of their choice, such as heuristic-based, simulation-based, or even formal tools. The participants are provided with small-sized designs to implement/test their techniques, inspect the performance by interfacing with AI-based tools, and subsequently improve scalability for large-sized designs.
Organizers:

![]()
③ IP protection
IP Protection and Security Evaluation
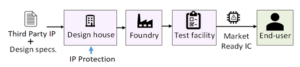
An attacker, anywhere in the globalized design flow, can reverse engineer the functionality of an IC and intellectual property (IP) as well as steal and claim ownership of the IP. An untrusted IC foundry may overbuild ICs and sell the excess parts in the gray market.
Our research addresses the security problems in IC design by developing novel design automation algorithms and circuit techniques to ensure the trustworthiness of an IP. Besides, our lab aims to evaluate the security of various IP protections, such as logic locking and hardware redaction.
- Multi-Objective Strategies for SFLL (paper): Stripped functionality logic locking (SFLL) techniques are resilient against I/O attacks and some structural attacks; however, the error rate is low, and it cannot sufficiently corrupt the functionality. This work aims to increase the error rate resulted by SFLL techniques.
- SPI Attack (paper): Sparse prime implicant (SPI) attack challenges all SFLL techniques and proposes that the defender needs to strategically choose protected input patterns.
- Evaluating Security of eFPGA: Embedded field programmable gate array (eFPGA) could be used for hardware redaction to hide circuit structure details. Our work evaluates the security of a hardware design redacted by eFPGA.
HeLLO CTF 2022
HeLLO CTF 2022 event is an open competition across the globe involving teams of students, faculty members, or industry practitioners, on evaluating the security of state-of-the-art countermeasures against attacks on hardware IP confidentiality, e.g., reverse engineering and cloning. Teams are given a suite of protected designs using open-source benchmarks for security evaluation. The specific countermeasures implemented into the protected designs include logic locking, obfuscation of state space, and hardware redaction. Our team from TAMU provides logic-locked designs and related evaluation on solutions from Red Teams.
SAHARA
Intel and the U.S. Defense Advanced Research Projects Agency (DARPA) have announced a three-year partnership to advance the development of domestically manufactured structured ASIC platforms through a partnership program named “Structured Array Hardware for Automatically Realized Applications” (SAHARA). The SAHARA program’s goal is to enable the design of custom chips that include state-of-the-art security countermeasure technologies, made available through a reliable, secure, domestic source of leading-edge semiconductors. Intel collaborates with Texas A&M University to develop a security countermeasure, Boolean Algebraic Transformation (BAT), to protect hardware IP on Intel’s structured ASIC, and then integrates BAT into Intel’s structured ASIC design flow.